Visibility Without Context Creates Risk
Most platforms stop at basic discovery. The result? Blind spots, noise, and random guesswork.
DLP enforces static rules—but lacks intelligence
DSPM floods your inbox—but can’t prioritize risk
Catalogs gather dust—too passive to drive action
IAM and access tools know identities—not intent
Your teams scramble to make sense of fragmented data. Meanwhile, sensitive assets sprawl unchecked—exposed, siloed, and under-leveraged.
Why KontxtualTM?
Get the Full Picture—and the Power to Act!
Other tools tell you where data is. Kontxtual tells you what it means.
We combine AI-driven contextual intelligence, multidimensional graphing, and orchestration to help you:
- Understand how sensitive data connects to identities, systems, and risk
- Automate the right response across the tools you already use
- Reduce effort, exposure, and risk—at scale
Trusted and ethical AI training data
Accelerated time-to-insight
Faster incident response
Smarter data governance
Enterprise-Grade Context That Changes the Game
KontxtualTM is trusted by global enterprises to reduce risk, unlock value, and drive operational clarity
What Happens When Context Comes First
Most tools stop at discovery. KontxtualTM keeps going—mapping, contextualizing, and automating responses across your stack.

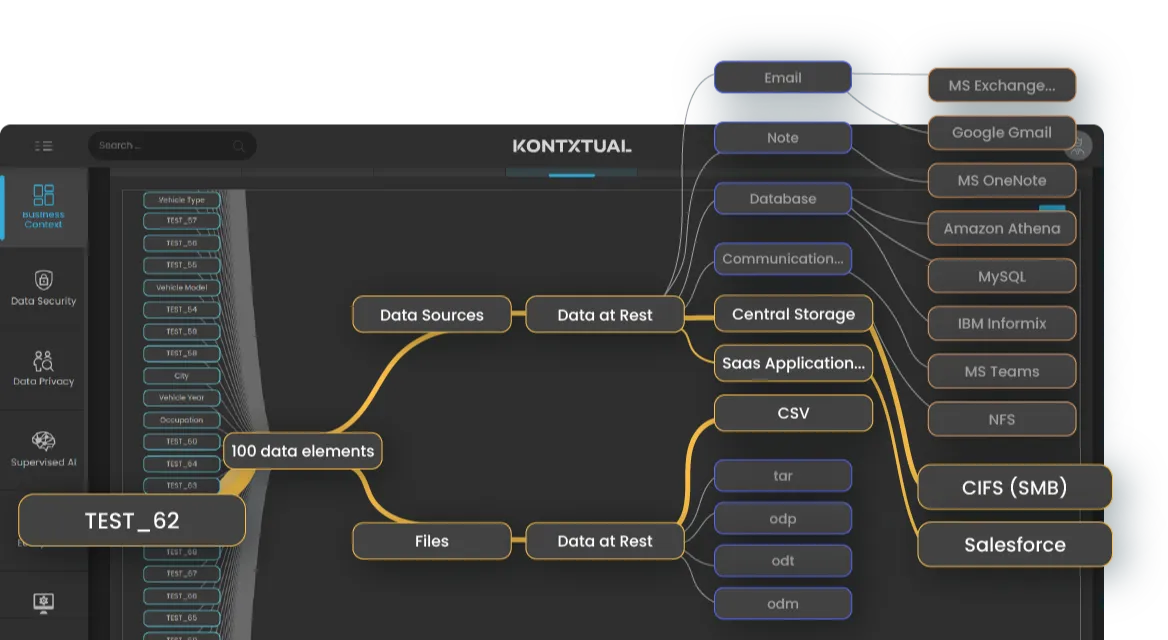
Start with a complete, real-time inventory of your sensitive data. Kontxtual continuously discovers data at rest and in motion—across every environment.
- Full, real-time inventory of sensitive data
- Structured, unstructured, cloud, SaaS, on-prem, mainframe
- No manual rules of tagging
Move beyond flat metadata. We build a contextual record per data element—tracking access, behavior, and exposure risk in real time.
- Multidimensional graph of all data objects
- Relationships, flows, exposure risks
- Contextual records updated continuously
- Semantic views driving contextualized records

Move from alerts to actions. With full context in hand, Kontxtual activates protection, compliance, and governance workflows automatically—using the tools you already have in place.
- Trigger policies through your existing tools
- Confidence scoring to reduce noise
- End-to-end workflow automation
From Inventory to Intelligence—KontxtualTM Moves You Forward
Whether you’re just finding sensitive data or enforcing global controls, KontxtualTM meets you where you are and moves you forward.
Use the 5-stage KontxtualTM Maturity Map to track your posture and plan your next step:



































.webp)